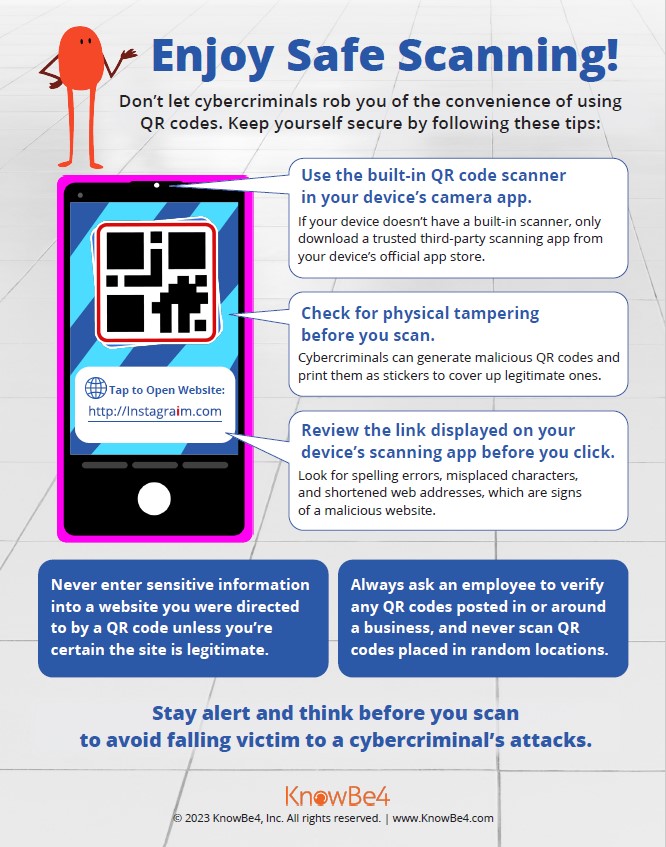
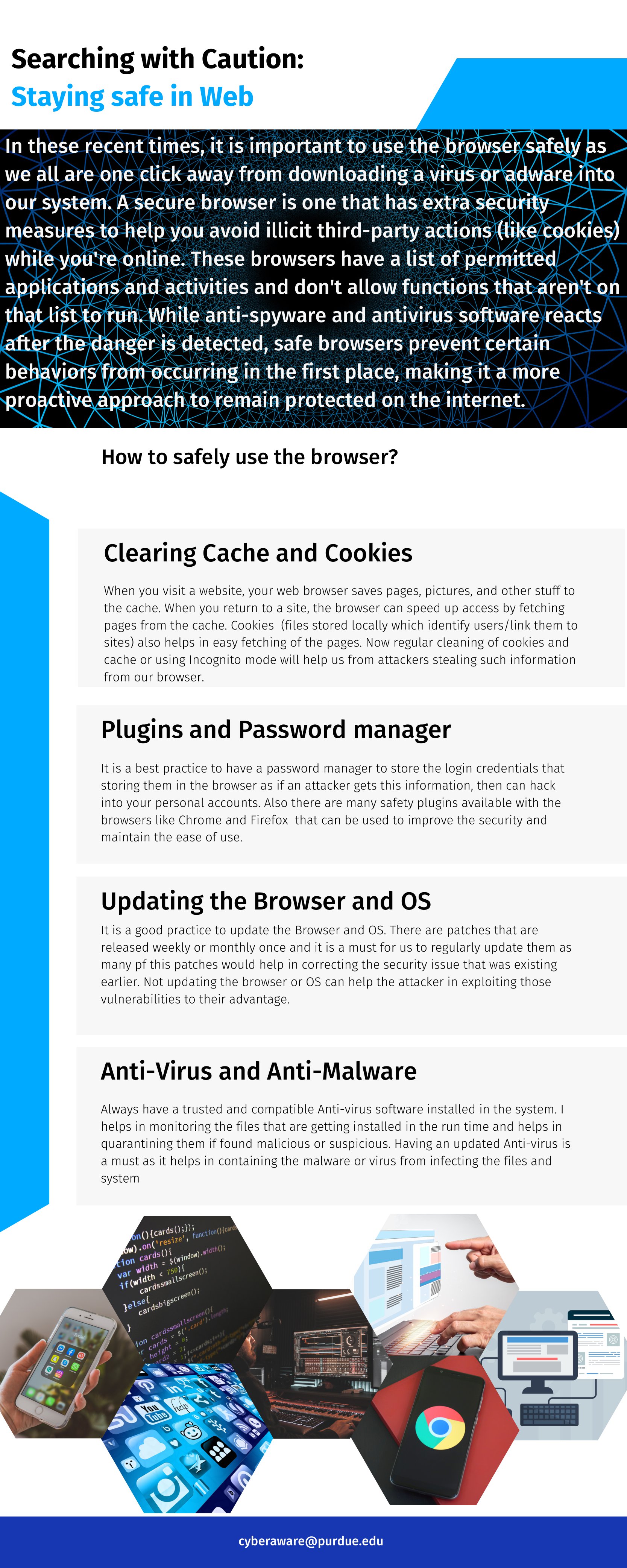
During the initial intrusion stage of a ransomware incident, the attacker has the advantage. It’s like the opening moves in a game of chess, when the white player advances first, choosing the Queen’s Gambit, perhaps. In a ransomware attack, as with a chess game, the attacker gets to choose how, when, and where he attacks an organization. He acts stealthy and cautious, as he waits for the perfect moment to strike.
The initial intrusion stage of a ransomware attack corresponds to the Reconnaissance, Weaponization, and Delivery phases of the Lockheed Martin Kill Chain (LMKC) and to the Reconnaissance, Resource Development, and Initial Access tactics of the MITRE ATT&CK Framework. During this period of activity, the attacker has the advantage.
However, once the attacker has achieved initial access to the defender’s network and entered the post-initial compromise stage, his control over the initiative and operational cadence weakens. The threat actor must loop through attack TTPs and move laterally in order to maximize impact and ensure the largest possible payout—without being detected and disrupted by defenders. The challenge for the attacker? Most of his techniques and activities are noisy, which increases his chances of getting caught.
At this point in a ransomware attack, defenders should control both the battle space and the environment. Yet this post-initial compromise stage is frequently overlooked by defenders. Using the chess analogy, this is where the midgame begins. The midgame corresponds to the Exploit, Installation, and Command & Control phases of the LMKC, and to the nine categories between and inclusive of the Execution and Command & Control tactics of the ATT&CK Framework.
In the midgame, the attacker must now operate within the defender’s environment, where the defender arguably should have full visibility, along with full control of data, identity, access and processes. If the defender knows and has visibility across her environment, she holds all the cards. As in a chess game, she controls the four squares in the middle of the board, giving her the ability to observe and respond to the moves of the attacker.
Unfortunately, most enterprises haven’t landed in the middle of the board, where they can watch for command and control (C2) beaconing, lateral movement, domain escalation, and other tell-tale signs of a ransomware attack. Instead, many enterprises continue to prioritize building a stout perimeter—a strategy that has repeatedly proven fallible against social engineering and phishing attacks, zero-day attacks, exploitation of software vulnerabilities, attacks on unsecured cloud assets and vulnerable mobile devices, and good old-fashioned brute force. Breaching the perimeter has become routine.
So, what is the alternative, and what is the solution? The answer: Deploy visibility, detection, and response measures inside the network environment, including on-premises, cloud, virtual, and hybrid environments, that you want to protect. This will give you command of the board, with the ability to see the attacker utilizing TTPs inside your environment throughout the attack process. Only then will you be able to disrupt the attack per the LMKC process.
Network Visibility and Detection Enable Proactive Ransomware Defense
The time between initial intrusion and ransomware deployment is crucial for defenders. This increasingly small-time interval provides defenders with the most opportunities to detect and disrupt attacks before threat actors can achieve their objectives. Why? Because threat actors, as stealthy as they try to be, have to communicate over the very corporate network they’re trying to compromise. Any transaction or activity remotely executed by the attackers must, by definition, be visible on the network. Ransomware attacks require at least five actions, all of which are visible from network telemetry. These five actions include:
- Movement and reconnaissance internal to the defender’s network to locate and identify the defender’s critical data artifacts for exfiltration and encryption;
- Establishment of an exfiltration path;
- Creation of a remote control framework, either through an independent C2 node with escalated privileges or through acquisition of an identity that provides escalated privileges;
- Replication, transmission, and exfiltration of the defender’s critical data out of the defender’s environment; and
- Command to execute, followed by execution of encryption routines to remotely encrypt the defender’s critical data.
In each of these actions, the network plays an essential role in threat detection because it’s where the attacker must operate. It’s where the attacker establishes C2 communication, expands his access, and escalates privileges. Thus, the network alone has the ability to observe and identify the ground truth of what attackers are doing. And unlike logs and endpoint detection and response (EDR) agents, the network can’t be evaded or disabled. An out-of-band and virtually undetectable network telemetry monitoring solution cannot be disabled because the attacker cannot gain access to a completely passive monitoring solution that works by viewing network traffic through taps or port spanning/mirroring.
Many early midgame attacker behaviors, such as C2 beaconing, discovery, lateral movement, privilege escalation, and domain escalation, are best detected on the network. I would argue that the only solution that can detect those actions and TTP categories is a network-based solution. To detect those activities without full network visibility, organizations will need a combination of both server syslogs or event logs, and analysis of processes from endpoints.
Later midgame ransomware activities, including data staging and data exfiltration, are also best detected on the network. Every MITRE ATT&CK Framework tactic associated with the midgame encompasses techniques that are only visible via network monitoring and analysis. Because most of these activities only take place in the East-West corridor, internal to the enterprise network, they can’t be detected by next-gen firewalls, which only monitor North-South traffic.
And on-premises, network-oriented perimeter solutions are unable to defend cloud assets in a hybrid, virtual or private cloud. In addition, because most TTPs are behavior-based, signature-based security tools such as IDS, IPS and antivirus cannot observe the attacker’s actions. Meanwhile, EDR tools only provide visibility into processes on endpoints, and thus, can only detect the behaviors originating from endpoints protected and monitored by an EDR agent.
Observing attacker behavior on the network requires the ability to monitor and analyze raw network traffic feeds, including packets, in real time. It is vital to understand and be able to observe three elements of network traffic:
- Protocols – Some types of protocols used by defenders, such as HL7 and ICCP, are industry specific; these could provide indications of atypical protocols used by attackers. These indications would also include the use of protocols frequently utilized by ransomware attackers, such as RDP.
- Traffic volume – The sheer volume of network traffic can be an indicator of an attack, especially if the high volume occurs at an unusual time.
- Volume and protocols combined – Trends in both volume and the use of protocols are an indicator of a gradual deployment of capabilities by ransomware actors in the defender’s business environment.
Decryption Matters
Defense against ransomware actors also requires the ability to decrypt encrypted network traffic (SSL, TLS 1.3, Kerberos, NTLM, MSRPC, LDAP, WINRM, SMBv3) for two reasons. One, in most environments, as much as 70% of an organization’s network traffic is encrypted. Two, since many ransomware actors often utilize custom or atypical encryption techniques to obfuscate their activity, defenders must be able to see both what should be encrypted and to identify unexpected encryption.
The ability to decrypt encrypted protocols like Kerberos, MSRPC, WINRM, and SMBv3 is essential to detecting PowerShell remoting, living off the land techniques, and lateral movement—activities that have been repeatedly documented in ransomware and other attacks. Only network visibility enables a full awareness of both the use and misuse of encryption in the defender’s environment.
It’s important to note that modern methods of decryption don’t decrypt any packets on the wire, so they preserve end-to-end encryption. They also don’t rely on “man-in-the-middle” or “break-and-inspect” approaches, so they don’t degrade network performance.
Granular, packet-level data and decryption capabilities are also essential to incident response and forensic investigation, as only full packets can tell incident responders exactly how a ransomware attack took place.
Prepare for Increased Ransomware Activity with Network Visibility
Ransomware attacks appear to be growing increasingly inevitable. Data from the ExtraHop 2024 Global Cyber Confidence Index shows that 95% of respondents experienced at least one ransomware incident in the 12 months prior to the survey and 91% paid at least one ransom over the same period. As the U.S. general election grows closer and geopolitical tensions continue to rise, cybersecurity experts predict ransomware attacks will only intensify.
In response, many organizations are investing in solutions that promise to detect initial intrusion tactics during the opening moves of the game. But some of that budget would be more wisely spent on solutions that detect post-initial compromise tactics where defenders have the greatest advantage. Network detection and response tools allow you to detect and respond to threats during nearly every stage of the attack chain, including post-initial compromise and beyond. When you have network visibility, you can protect against a wide variety of advanced threats, including ransomware, with greater accuracy, and you can respond with confidence.